Why do Hackers focus on Medical Records?
The HIPAA Journal provides a great deal of data about hackers and medical records, but sometimes it is only possible to scratch the surface of healthcare data breach statistics. This article takes a deeper look at the available information to identify common causes of hacking/IT incidents.
Why Focus on Hackers and Medical Records?
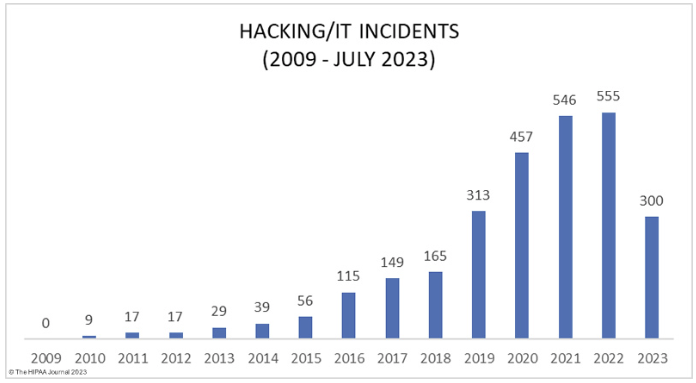
The reason for focusing on hackers and medical records is that, on the surface, the number of reported hacking/IT Incidents affecting more than five hundred individuals has increased significantly over the past decade. This has led to some startling headlines on health IT websites, which could influence how security resources are allocated.
There are several reasons for the increased number of reported hacking/IT Incidents other than an actual increase in hacking/IT Incidents. These include that security teams and technologies have got better at detecting hacking incidents and that ransomware attacks are included in the statistics even if no data breach has occurred (this is discussed in greater detail later).
However, one of the most likely reasons for the large increase in the number of reported hacking/IT Incidents affecting more than five hundred individuals is that databases have grown in size as healthcare providers adopt the cloud and combine PHI from individual on-premises databases to a centralized database in the cloud. The next section further supports this theory.

Get The FREE
HIPAA Compliance Checklist
Immediate Delivery of Checklist Link To Your Email Address
Please Enter Correct Email Address
Your Privacy Respected
HIPAA Journal Privacy Policy
How the Smaller Data Breaches Stack Up
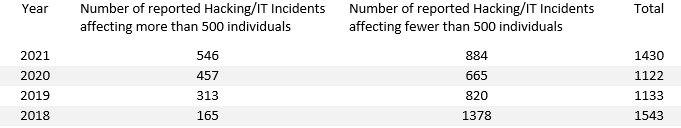
Although HHS does not publish an online database of reported data breaches affecting fewer than five hundred individuals, the breaches are summarized in HHS’ Annual Reports to Congress. At present, the Annual Reports for 2018 to 2021 are available online, and it is from these reports we have extracted the reported hacking/IT Incidents affecting fewer than five hundred individuals.
While it is important not to take this small sample of data out of context, and notwithstanding that 2018 may have been an exceptional year for reported hacking/IT Incidents affecting fewer than five hundred individuals (*), it is worth noting that there were more hacking/IT Incidents reported in total in 2018 than in 2021, and also more in total in 2019 than there were in 2020.
(*) Unfortunately, the Annual Reports prior to 2018 are no longer accessible via the HHS website; and, as the 2021 Annual Report to Congress was only delivered in February 2023, it will be some time before it is possible to tell whether the total number of reported hacking/IT Incidents increases, falls, or remains consistent with those reported between 2018 and 2021.
Hackers and Medical Records Held to Ransom
In the context of taking a deeper look at data about hackers and medical records, it is important not to ignore how medical records held to ransom are accounted for in the HHS’ Breach Report. Generally, ransomware attacks are considered to be disclosures not permitted by the Privacy Rule due to “unauthorized individuals taking possession or control of the information”.
Whether or not a ransomware attack is a notifiable event is a “fact-specific determination” according to HHS’ Ransomware Fact Sheet. However, unless a covered entity or business associate can demonstrate a low probability that PHI has been acquired or viewed in accordance with 45 CFR §164.402(2), (which is hard to prove in most ransomware attacks), the event is notifiable.
When reporting a ransomware attack, the Help section of the Breach Portal states, “Only select hacking/IT Incident if ePHI was impermissibly accessed through a technical intrusion.” Nonetheless, even though there may be no evidence to suggest PHI has been acquired or viewed – but the possibility cannot be ruled out – ransomware attacks are most often entered as hacking/IT Incidents.
How Many Hacking Events are Attributable to Ransomware Attacks?
When reviewing the Breach Report, visitors have two options – view the cases currently under investigation or view an archive of closed cases. The archive provides a description of what happened for most of the closed cases, and by analyzing the descriptions, it is possible to establish how many events reported as hacking/IT Incidents are attributable to ransomware attacks.
To get an idea of how many reported hacking events are attributable to ransomware attacks, the last two hundred closed cases in which the event “Type” was entered as a hacking/IT Incident were analyzed. This is the result of the analysis:
- 37.5% of hacking/IT Incidents were attributable to unspecified cyberattacks
- 33.5% of hacking/IT Incidents were attributable to ransomware attacks
- 29% of hacking/IT Incidents were attributable to phishing emails
Unfortunately, the analysis is inconclusive because, while conducting the analysis, multiple mis-categorizations were identified – for example, ransomware attacks categorized as “Theft” and phishing emails categorized as “Unauthorized Disclosures”. Additionally, it is well chronicled that 91% of cyberattacks (including ransomware attacks) start with a phishing email.
Common Causes of Data Breaches in Healthcare
By further analyzing the archive database, it is possible to identify common causes of data breaches in healthcare that can help security teams better allocate resources. Therefore, it may not only be necessary to improve users’ resiliency to phishing emails, but also to better secure connected EMRs and implement measures to prevent the misconfiguration of cloud servers.
Returning specifically to hackers and medical records, it will soon be necessary for healthcare security teams to comply with CIRCIA (Cyber Incident Reporting for the Critical Infrastructure Act). The reporting requirements of CIRCIA mean that attempts to hack a database containing PHI will have to be reported to CISA regardless of whether the attempts are successful or not.
While the increased reporting requirements and the detail required will undoubtedly be burdensome, they should result in more accurate and complete data about hackers and medical record thefts – helping security teams better identify gaps in their security defenses and better allocate resources to address threats and vulnerabilities.